Configuring Secured (HTTPS) Web
By default, the device allows remote management (client) through HTTP and HTTPS. However, you can enforce secure Web access communication by configuring the device to accept only HTTPS requests.
By default, servers using TLS provide one-way authentication. The client is certain that the identity of the server is authentic. However, when an organizational Public Key Infrastructure (PKI) is used, two-way authentication (TLS mutual authentication) may be desired; both client and server should be authenticated using X.509 certificates. This is achieved by installing a client certificate on the management PC and loading the Certification Authority's (CA) root certificate to the device's Trusted Certificates table (certificate root store). The Trusted Root Certificate file may contain more than one CA certificate combined, using a text editor.
|
●
|
For secure management through the device's default management network interface (i.e., OAMP Application Type in the IP Interfaces table), the device uses the default TLS Context (Index #0 and named "default"). However, for secure Web and REST access using additional management interfaces configured in the Web Interfaces table (see Configuring Web Interfaces), you can use any TLS Context. |
|
●
|
The 'Secured Web Connection (HTTPS)' parameter (mentioned below) is also applicable to REST-based management. |
|
➢
|
To configure secure (HTTPS) Web access: |
|
1.
|
Open the Web Settings page (Setup menu > Administration tab > Web & CLI folder > Web Settings), and then do the following. |
|
●
|
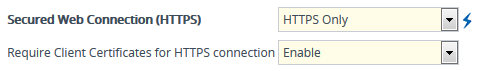
From the 'Secured Web Connection (HTTPS)' drop-down list, select HTTPS Only. |
|
2.
|
If you want to configure secured management through a user-defined Web Interface (see Configuring Web Interfaces) instead of the default management network interface (OAMP in the IP Interfaces table), then make sure that you assign it a TLS Context and enable it for HTTPS Only. |
|
3.
|
(TLS Mutual Authentication Only) In the TLS Contexts table (see Configuring TLS Certificate Contexts), select the required TLS Context (see following note), and then click the Trusted Root Certificates link located below the table; the Trusted Certificates table appears. |
If you are securing management through the default management network interface (i.e., OAMP in the IP Interfaces table), then you need to select the default TLS Context (Index #0, which is named "default"). If you are securing management using a configured Web Interface (see Configuring Web Interfaces), then select the TLS Context that you assigned the Web Interface.
|
4.
|
(TLS Mutual Authentication Only) Click the Import button, and then select the certificate file that was issued by the CA and which you want to import into the device's Trusted Root Certificates store. |
|
5.
|
Restart the device with a save-to-flash for your settings to take effect. |
When a user connects to the secured Web interface of the device:
|
■
|
If the user has a client certificate from a CA that is listed in the device's Trusted Root Certificate file, the connection is accepted and the user is prompted for the login password. |
|
■
|
If both the CA certificate and the client certificate appear in the Trusted Root Certificate file, the user is not prompted for a password. Therefore, this provides a single-sign-on experience; authentication is performed using the X.509 digital signature. |
|
■
|
If the user doesn't have a client certificate from a listed CA or doesn't have a client certificate, connection is rejected. |
|
●
|
The process of installing a client certificate on your PC is beyond the scope of this document. For more information, refer to your operating system documentation and consult with your security administrator. |
|
●
|
The root certificate can also be loaded through the device's Auto-Update mechanism, by using the [HTTPSRootFileName] parameter. |
